The Everest ransomware gang has claimed a successful hack of Taiwanese technology company ASUS.
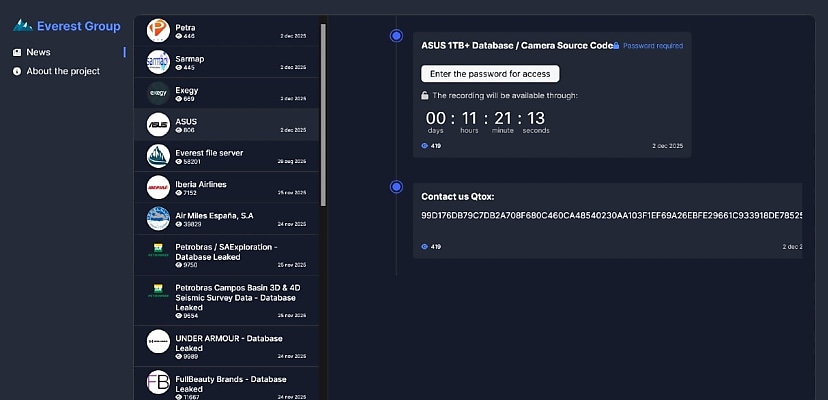
The hackers made the allegation in a 2 December post to their darknet leak site, claiming to have gotten hold of a database more than one terabyte in size, and “Camera Source Code”.
Everest shared details on how ASUS can contact the hackers, alongside a countdown when the data is expected to be published, with 11 hours at the time of writing, or approximately 4 December.
Everest has not shared any sample data, nor its ransom demand.
Cyber Daily has reached out to ASUS for comment on the hackers’ allegations.
Everest has a history of going after high-end targets and was responsible for a recent incident that caused widespread disruption to several European airports in September. The group claimed responsibility for an attack that targeted Collins Aerospace and its vMUSE passenger processing system a month later.
The attack caused flight delays and cancellations and forced airline staff to turn to pen-and-paper booking procedures.
Soon after it claimed responsibility, Everest began leaking not only data but also details of how it was able to compromise Collins Aerospace’s network.
“The company’s IT staff had the opportunity to learn about the extent of the breach in advance, before critical services were shut down, which could have influenced subsequent decisions and the consequences for both passengers and the airline,” Everest said in late October.
“After investigating the access, we determined that this FTP resource is connected to Collins Aerospace’s infrastructure and is used in air transportation processes.
Over the next few days, Everest allegedly downloaded what data it could before the unauthorised access was detected, and the hackers were ejected. At the same time, Everest analysed what it had exfiltrated before contacting RTX – Collins Aerospace’s owner – via the RTX.com vulnerability reporting portal.
Negotiations began, but the process apparently broke down, leading Everest to publish the data it had accessed.
Everest said it no longer deploys ransomware, but that is definitely how the group started out in 2020.
Since then, however, it has shifted to acting more as an initial access broker, according to some reports, but the group has certainly claimed its fair share of high-profile victims, including the 2021 Colonial Pipeline attack. It is actively recruiting partners via its leak site.
The group – thought to be Russian-speaking – uses a variety of initial access methods, ranging from exploiting weak or stolen credentials (which was likely the case with Collins Aerospace), insider recruitment, and remote access tools.
Everest’s most recent Australian victim was applied behavioural science firm Evidn, which was listed by the hackers in January 2025.
ASUS is one of the largest makers of computers and PC parts in the world and makes everything from laptops to mobile phones, motherboards to graphics cards.
David Hollingworth
David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.