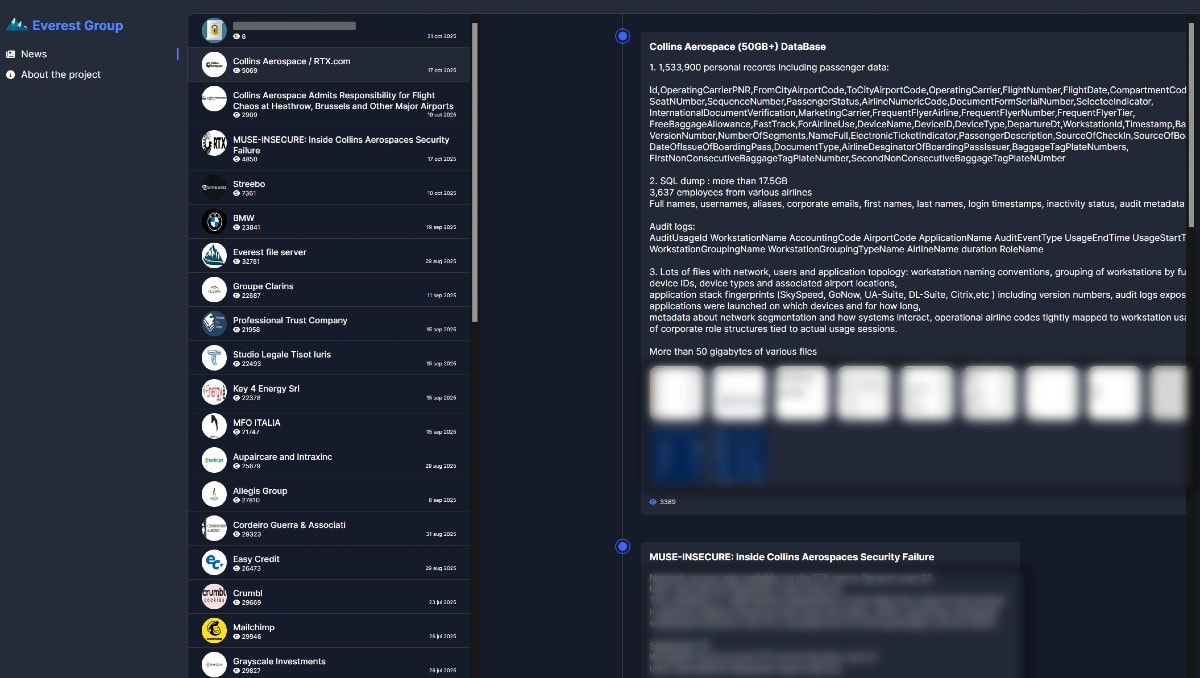
The hackers responsible for major disruptions across several European airports last month have escalated their claims in the wake of the attack, saying they have a mountain of passenger and employee data to publish in the coming days.
The Everest Group, which claimed responsibility for the September Collins Aeropspace attack on 17 October, has also laid out its version of the incident’s timeline, alleging that it had FTP access to the company’s vMUSE back end as early as 10 September.
Data leak?
Everest claims to have exfiltrated three discrete datasets, including 1,533,900 personal records totalling more than 50 gigabytes, a 17.5-gigabyte SQL dump with the details of “3,637 employees from various airlines”, and a 50-gigabyte set of data comprised of “various files”, which the hackers claim includes the following:
“Lots of files with network, users and application topology: workstation naming conventions, grouping of workstations by functional roles, device IDs, device types and associated airport locations, application stack fingerprints (SkySpeed, GoNow, UA-Suite, DL-Suite, Citrix, etc ) including version numbers, audit logs exposing which applications were launched on which devices and for how long, metadata about network segmentation and how systems interact, operational airline codes tightly mapped to workstation usage, clear visibility of corporate role structures tied to actual usage sessions.”
The employee data allegedly includes both full names and usernames, aliases, email addresses, login and inactivity status, and audit metadata, while the larger set includes passenger data such as frequent flyer and airline details, travel data, seat numbers, and more. That set, however, does not appear to include passenger names, only passenger ID numbers.
Early access?
Everest claims to have gained access to vMUSE – Collins Aerospace’s check-in and boarding software – on 10 September, and recently shared the login details to prove the group’s allegations.
“The company’s IT staff had the opportunity to learn about the extent of the breach in advance, before critical services were shut down, which could have influenced subsequent decisions and the consequences for both passengers and the airline,” Everest said in its updated leak post.
“After investigating the access, we determined that this FTP resource is connected to Collins Aerospace’s infrastructure and is used in air transportation processes.”
Over the next few days, Everest said it downloaded what data it could find before the unauthorised access was detected, and the hackers lost access. At the same time, Everest analysed what it had exfiltrated before contacting RTX via the RTX.com vulnerability reporting portal.
At this point – on 16 September – Everest claims it was contacted by a representative of Collins Aerospace. It’s worth noting that the initial disruption to air travel occurred on 19 September.
“Collins Aerospace promptly contacted us through a negotiator on the QTox messenger,” Everest said.
“We sent a list of the stolen data, our full terms, and received a promise to investigate.”
Failure to communicate
Negotiations appear to have broken down between 18 and 24 September, and according to the hackers, “Collins Aerospace shut down a number of servers responsible for air travel processes, officially blaming it on unspecified ransomware”.
“We would like to emphasise: the server shutdown led to a significant disruption in air travel and operations, affecting thousands of flights and passengers,” Everest said.
“In our opinion, the situation could have been resolved differently, without creating additional problems for passengers; there was no objective need to resort to measures that caused widespread disruptions.”
In response to Collins Aerospace’s ransomware claims, Everest claimed that it does not deploy ransomware and hasn’t done so “for many years”, despite being tracked as a ransomware operator by many researchers and analysts.
Alongside screenshots of file trees and passenger and employee data, Everest also shared what it claims are screenshots of its negotiations with Collins Aerospace. The company was allegedly given a ransom deadline of 12 October.
Cyber Daily has sought comment from RTX, Collins Aerospace’s parent company, but has yet to receive a response.
Official timeline
On 19 September, RTX first said it was aware of “a cyber-related disruption” to Collins Aerospace’s systems, as both Brussels Airport and Berlin Brandenburg International Airport reported increased waiting times and delays due to the incident.
On the same day, in a Form 8K filing to the US Securities and Exchange Commission, RTX said it “became aware of a product cyber security incident involving ransomware on systems that support its Multi-User System Environment (“MUSE”) passenger processing software”.
On 20 September, Heathrow Airport was forced to move to a backup system, and Dublin Airport reported similar disruptions between 21 and 22 September.
On or before 24 September, UK authorities arrested and then released a 40-year-old suspect, with the National Crime Authority saying its investigations were ongoing.
By 29 September, a replacement system – also supplied by Collins Aerospace – was rolled out at Brussels Airport, effectively bringing the period of travel disruption to an end.
Despite the hackers’ claims that no ransomware was deployed, the director of the UK’s National Cyber Security Centre (NCSC), Dr Richard Browne, said on 23 September that the NCSC knew the attacker and the strain of malware used.
“We have all of the technical details from the incident, and we know, or we believe we know, who the actual group is. Precisely where they’re based is always going to be interesting and difficult to try and work out,” Browne said.
“The other thing to keep in mind here is that we know the malware strain used. So this is the wholesaler or the reseller of the malware, we don’t know who actually conducted the incident.”
Brown added that he believed the attacker to be merely an affiliate of the ransomware group concerned.
Who is Everest?
Everest may say it no longer deploys ransomware, but that is definitely how the group started out in 2020.
However, since then, it has apparently shifted to acting more as an initial access broker, according to some reports, but the group has certainly claimed its fair share of high-profile victims, including the 2021 Colonial Pipeline attack. It’s also targeted NASA and the Brazilian government.
The group – thought to be Russian-speaking – uses a variety of initial access methods, ranging from exploiting weak or stolen credentials (which looks to be the case with Collins Aerospace), insider recruitment, and remote access tools.
The group’s most recently listed Australian victim was Queensland-based behavioural science Evidn firm in January 2025.

David Hollingworth
David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.