Security

Brisbane GP cyber attack sparks Services Australia data verification
Services Australia has commenced an investigation into a cyber attack on Brisbane GP and cancer treatment clinic Top ...

Australian telcos have stopped 336.7m scam texts since July 2022
The Australian Communications and Media Authority has worked with telcos to stop a staggering number of scam texts.

Customers of Sydney radiology clinic left uninformed following cyber attack
A Sydney-based radiology clinic has angered its patients after it failed to inform them of the details of a cyber attack ...

Australian Cyber Crime Monthly Report: November 2023
Cyber Daily’s round-up of ransomware attacks, data breaches, and other cyber incidents from around the country over the ...

OAIC alleges Australian Clinical Labs hack resulted from lacklustre security measures
The Office of the Australian Information Commissioner (OAIC) has alleged that leading pathology company Australian ...

Ukrainian hacktivist attack finds Russian propaganda agency cherrypicking Western media
Ukrainian hacktivists have leaked data belonging to a Russian propaganda agency known for reposting carefully curated ...

Okta reveals more details of October data breach – it’s worse than you think
All Okta Help Centre customer support users were impacted by the company’s October data breach.

Trio of major ownCloud vulnerabilities sparks ACSC critical alert
A critical alert has been issued by the Australian Cyber Security Centre (ACSC) after it discovered a trio of major ...

PwC security questioned as firm’s head of risk fooled by fake email
Ever-troubled consulting firm PwC has launched an investigation after a fake email ironically fooled the company’s head ...
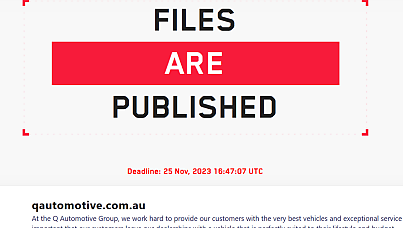
LockBit ransomware gang claims hack on Queensland-based Q Automotive Group
Hackers claim to have customer and internal data totalling more than 50 gigabytes.

Hacked healthcare organisation forced to shut down emergency rooms, divert ambulances
Emergency rooms across the US have been shut down following a cyber attack, forcing hospitals to reschedule elective ...

Flaw in Google Workplaces could lead to theft of data and emails
Threat researchers have uncovered a design flaw in Google’s domain-wide delegation feature.

Report: Cyber attacks lead to job creation in majority of cases
Australian boards are learning the hard way that more expertise is needed to combat growing cyber threats.
