Share this article on:
Powered by MOMENTUMMEDIA
For breaking news and daily updates,
subscribe to our newsletter.
Australian and US authorities break down how the Play operation works, from tools to tactics.
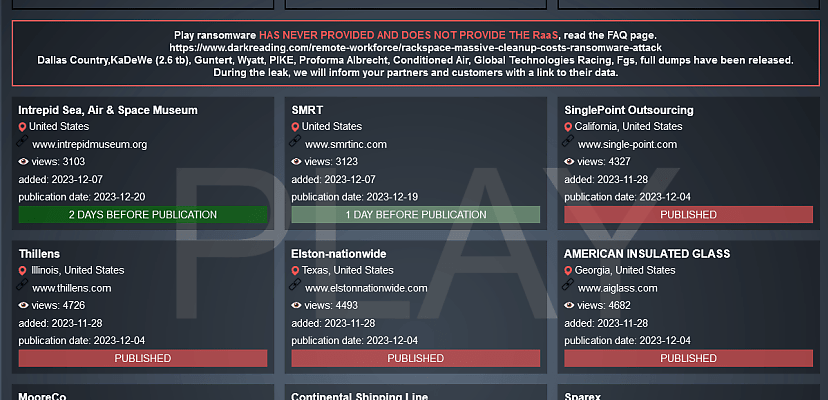
The Australian Cyber Security Centre (ACSC) has joined forces with the US Cybersecurity and Infrastructure Security Agency (CISA) and the FBI to publish a joint cyber security advisory outlining the techniques, tactics, and procedures of the Play ransomware gang.
The Play group has been active since at least June 2022, though the very earliest victim listed on its darknet leak site dates back to November of the same year.
Regardless, in that time, Play has racked up an impressive list of victims – the FBI says it is aware of about 300 organisations that have fallen foul of the gang.
Unlike some other gangs, Play operates only on its own behalf and is a closed group.
“We are not an affiliate program,” Play said in its FAQ, “this guarantees the secrecy of deals, there are no third parties who decide to do otherwise than their affiliate partners”.
In addition, the group has a banner on the top of its leak site homepage declaring, “Play ransomware HAS NEVER PROVIDED AND DOES NOT PROVIDE THE RaaS”, or ransomware-as-a-service.
The gang’s most recent Australian victim was the Victoria-based FGS Hardware, whose data (204 gigabytes of “Private and personal confidential data, clients documents, agreements, budget, HR, tax, finance information and etc”, according to Play) was published on 21 November, presumably after ransom negotiations failed.
TTPs
The Play ransomware gang typically gains initial network access by exploiting known, web-facing vulnerabilities in FortiOS and Microsoft Exchange and through valid accounts where it can. Remote Desktop Protocol and VPNs have also been taken advantage of.
The gang uses a wide range of tools for moving about victim networks, including AdFind for Active Directory queries and the Grixba info stealer to map out networks and look for AV software. GMER, IObit, or PowerTool disable any such software found, while log files are also deleted. Play has also been observed using PowerShell to target Microsoft Defender.
Unlike some gangs, Play both encrypts and exfiltrates data, splitting it up into easily acquired chunks using WinRAR before leaving the usual ReadMe ransom note. Data is transferred off the network via WinSCP. The encrypted files that remain on the victim’s machine are given a .play extension, and the note directs victims to contact the gang at a German email address. No ransom amount is initially given.
The gang itself goes into more detail in its FAQ.
“The first thing you need to do is leave your contact in the feedback form, after that we will contact you and discuss the terms of the deal,” Play said, before listing the following steps: the victim sends an encrypted file back to the gang, which proves it can safely decrypt it, then payment is discussed, and another set of files decrypted to show the gang’s apparent good faith.
If a victim pays (in cryptocurrency as a rule), Play said it will delete all the stolen data from its own systems before sending the victim a decryptor.
If the ransom is not paid, the victim’s files remain encrypted, while the stolen files are then shared on Play’s leak site.
The advisory notes that many of the tools that Play uses are otherwise legitimate pieces of software, including AdFind, IObit, and Cobalt Strike. The latter is a penetration testing tool that has been widely disseminated in the hacking community.
The advisory also lists a series of mitigation measures that organisations can take, including enabling multifactor authentication and keeping all software and firmware up to date across an organisation’s network. It’s all boilerplate stuff, but it’s these details that can stop a ransomware attack in its tracks.
You can read the full advisory, which includes a list of indicators of compromise, here.

David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
Be the first to hear the latest developments in the cyber industry.