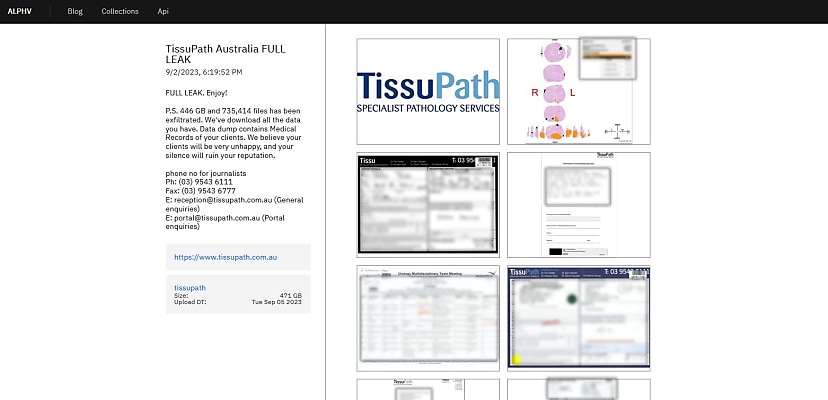
The data totals 471 gigabytes of information, and the ALPHV ransomware gang has posted some sample images of what’s inside the leak.
“FULL LEAK. Enjoy!” the gang said on its leak site.
“P.S. 446 GB and 735,414 files has been exfiltrated. We’ve download [sic] all the data you have. Data dump contains Medical Records of your clients. We believe your clients will be very unhappy, and your silence will ruin your reputation.”
TissuPath posted a notice on its website earlier this week alerting its patients of the hack.
TissuPath said that no billing information was impacted but that some patient data was affected. The company did not state how many of its patients were impacted by the hack, but it did say that the data related to referrals made between 2011 and 2020.
“The TissuPath Pathology specimens and referrals are for suspected cancer patients,” TissuPath said. “Such data is retained for 20 years and reported as per National Pathology Accreditation Advisory Council (NPAAC) specifications.”
At the time, TissuPath reported that a threat actor had gained initial access via a third-party supplier, one of whose storage drives had been accessed due to “a vulnerability on their remote access toolkit (RAT)”. From there, the actor was able to access admin accounts, which in turn let them access TissuPath’s network.
The third party was not mentioned in the initial report.
However, the ABC is reporting that the breach was related to a cyber security incident at Victorian IT company Core Desktop. It has seen a letter from the company, sent to its clients, informing them of the breach.
“Our cyber forensic team do not have a firm understanding of the origins of the entry, but initial suggestions are that it was from a targeted client-side phishing attack which infiltrated our control systems, impersonated privileged accounts and encrypted some servers,” the ABC reported the letter said.
“They appear to have acted in a focused fashion and threatened a small number of Core Desktop clients.”
“We’re not really aware of what information has been compromised,” Core Desktop’s managing director, Rod Bloom, told the ABC, “it’s not our data, so we don’t know”.
The breach is being considered as very serious, and both the Australian Signals Directorate and its Australian Cyber Security Centre are monitoring the incident.
Indeed, the nature of the affected data is deeply sensitive. The sample files include a prostate scan, doctor referrals, and doctors’ meeting notes. Patient names and addresses feature prominently, as well as individual diagnoses of breast and testicular cancer, and even a liver biopsy. TissuPath had said the details of “suspected cancer patients” were affected.
The national cyber security coordinator, Air Marshal Darren Goldie, told the Guardian that he is monitoring the situation.
“Given the sensitivities of the incident, the national cyber security coordinator is overseeing a whole-of-government response to the Tissupath incident,” Goldie said.
The Core Desktop data breach has impacted three other organisations: real estate agent Barry Plant’s Blackburn office, strata provider Strata Plan, and law firm Tisher Liner FC Law.
But it is the detailed patient data – all 471 gigabytes worth – that is the most disturbing aspect of the leak.
Senetas chief executive Andrew Wilson said that the different impacts on the affected organisations likely hide a harsh lesson to learn.
“This attack has had one common factor but strikingly disparate outcomes,” Wilson said via email. “On the one hand, we have Tissupath in the position of reporting compromised, highly sensitive personal data. On the other, Strata Plan’s confident response that its customers can ‘rest assured’ that their data is secure.”
“From this, we can infer one big insight - Strata Plan likely strongly encrypted its data beforehand, and Tissupath did not. Even though this is a ransomware attack, which encrypts a victim company’s data, the fact remains that it’s useless to the attackers if it was already encrypted before the attackers got there.”
“It’s also striking that, yet again, Australian citizen’s personal data is being held to ransom, not because of a sophisticated attack but simple mistakes like falling for a phishing email. We desperately need tougher legislation that will mandate that all personal data is encrypted both at rest and in motion as a last line of defence. We also, as a nation, need to have assurances that once data is captured by a private business, that the data has an expiry date. The phrase “data is the new oil’ has come to dominate business thinking.
“As a society, we have learned the hard way that we need very strict rules about who can be trusted to have a tanker full of oil and how it should be transported and stored. It appears the new oil needs a new set of regulations to govern it, before we will see meaningful change.”
David Hollingworth
David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.