According to cyber security firm Volexity, the malware, named SharpTongue, is an activity cluster that overlaps with an adversarial collective known as Kimsuky.
Historically, SharpTongue targets individuals working for organisations in the US, Europe, and South Korea who "work on topics involving North Korea, nuclear issues, weapons systems, and other matters of strategic interest to North Korea", according to Volexity researchers Paul Rascagneres and Thomas Lancaster.
The latest espionage effort employs the extension, named Sharpext, to steal email data.
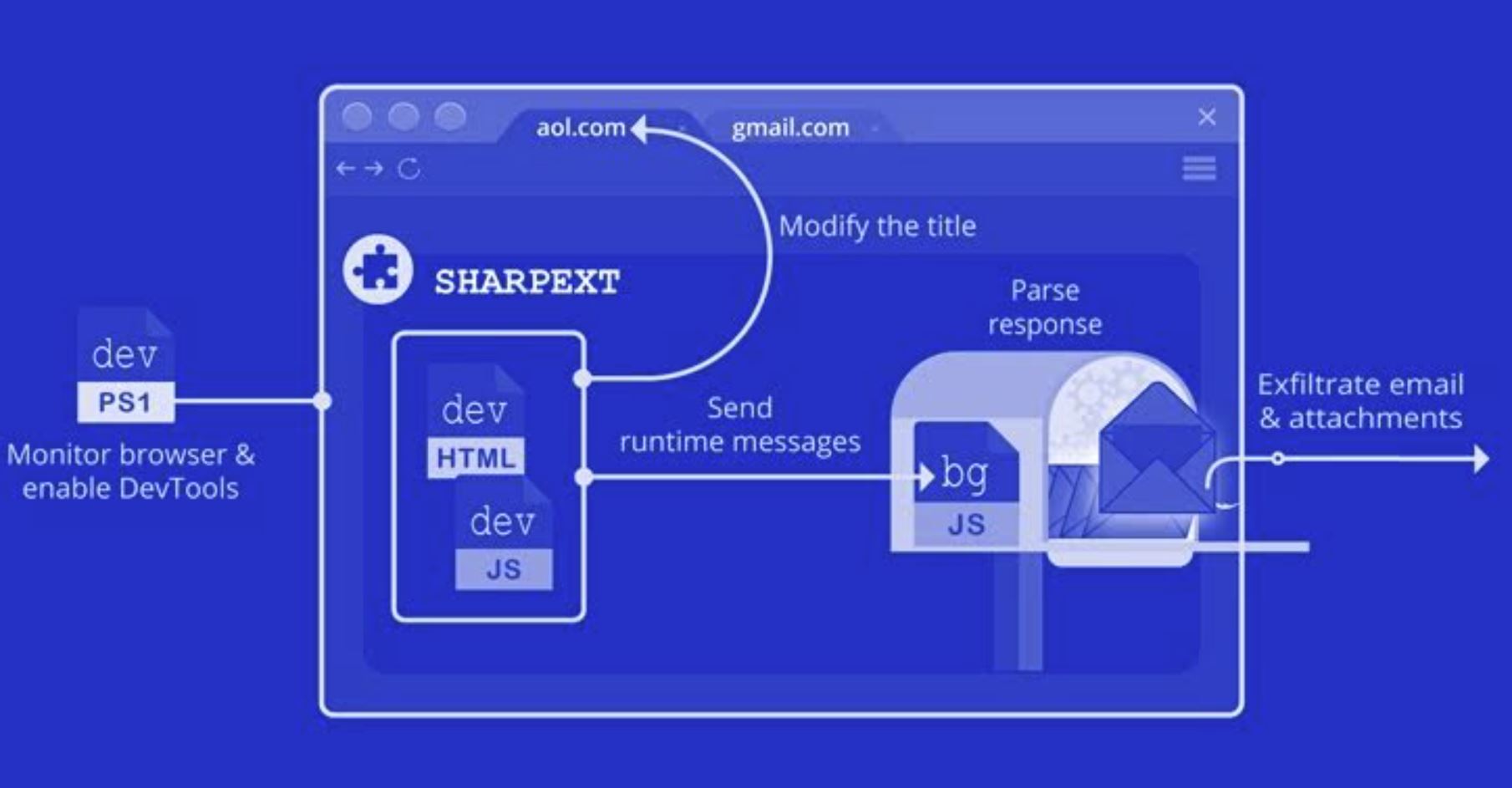
"The malware directly inspects and exfiltrates data from a victim's webmail account as they browse it," the Volexity researchers stated.
The mail-theft malware is designed to harvest information from Gmail and AOL sessions, and targeted browsers including Google Chrome, Microsoft Edge, and Naver's Whale browsers.
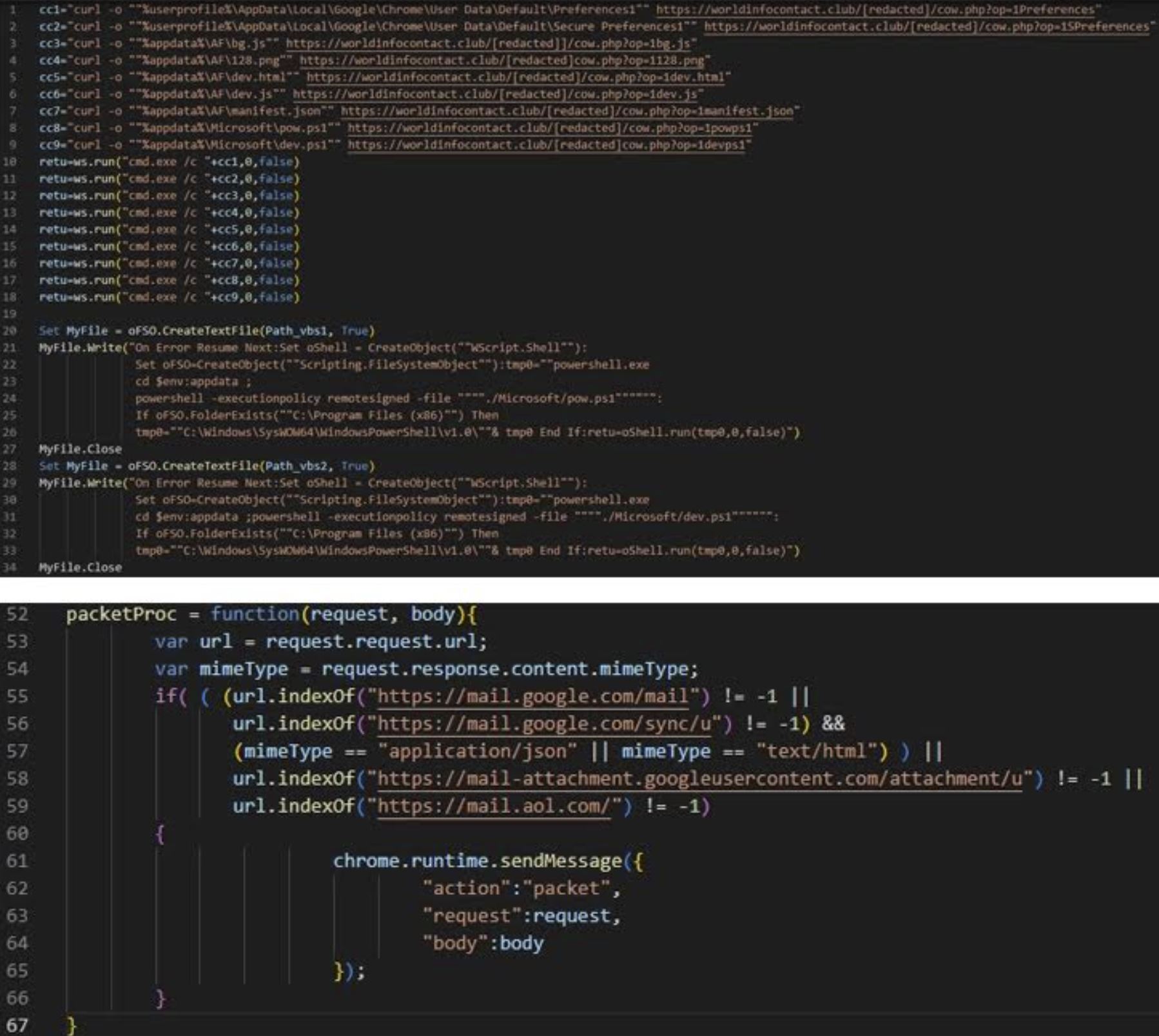
After a successful breach of a target Windows system, the spyware add-on is installed via a remote server. The malicious browser extension is designed to replace the target browser's preferences and secure preferences files with those received from the remote server.
The malware tool enables the DevTools panel within the active tab to steal email and attachments from a user's mailbox, while working towards hiding warning messages about running developer mode extensions.
According to Volexity, the campaign is "quite successful" in terms of the attacker's ability to "steal thousands of emails from multiple victims through the malware's deployment".
"This is the first time Volexity has observed malicious browser extensions used as part of the post-exploitation phase of a compromise.
"By stealing email data in the context of a user's already-logged-in session, the attack is hidden from the email provider, making detection very challenging," the Volexity researchers added.
Kimsuky's use of extensions for its targeted attacks is not new. The actor was observed using a Chrome plug-in as part of a campaign called Stolen Pencil to infect victims and steal browser cookies and passwords in 2018.
Recently, the Volexity researchers noted that the Kimsuky threat actor has been connected to intrusions against political institutions located in Russia and South Korea several months ago, during a campaign to deliver an updated version of a remote access Trojan known as Konni.
[Related: AFP charges Melbourne man for building and distributing global spyware tool]

