Last year, there was one ransomware attack every 11 seconds. This year, the rate is expected to double.
This stark figure, from researchers at Cybersecurity Ventures, makes it clear ransomware is one of the biggest threats facing organisations today and that traditional cybersecurity approaches are failing to keep pace.
The reason these attacks are increasing so rapidly is because they’re successful and there is money to be made. According to the Australian Cyber Security Centre’s latest Annual Threat Report, almost 500 ransomware incidents were reported last financial year – a 15 percent increase from the previous year.
With ransom demands ranging from thousands to millions of dollars, every successful attack represents a significant pay-day for the criminals. As long as the ransomware business model remains this lucrative, the threat will only continue to grow, becoming more sophisticated and more disruptive.
Enterprises trying to stave off these attacks with only traditional infrastructure security measures have three critical things going against them.
The first is the asymmetric nature of the challenge. While businesses need to stop 100 percent of attacks to remain secure, attackers only need one phishing email to hit its mark to completely compromise the victim.
The second is the increasingly digital-by-default way of working that’s become the norm. As more employees work remotely, the attack surface hackers can exploit grows exponentially.
The final factor stacked against enterprises is the increasing sophistication of ransomware gangs as they seek to cause the most disruption possible and ensure their ransom demands are met. One example of this is attackers targeting backup data to ensure the victim’s ability to restore operations itself is severely – if not entirely – halted.
To even the odds against this stacked deck, a new approach is needed. That approach is Zero Trust Data Security.
While traditional infrastructure security is important, its primary focus is trying to keep the attackers out of the business. If an attacker evades these defences, however, they can have free reign to move laterally, compromise credentials, and cause ongoing damage to an organisation.
Zero Trust Data Security, on the other hand, trusts no person or system and assumes a breach has already occurred. The focus is on keeping business-critical data secure even in the event of an attack. This approach allows for resilience against cyber attacks, malicious insiders, and operational disruptions.
Data Security is the future of cyber security. It is an approach that understands when you protect your data, you protect your business.

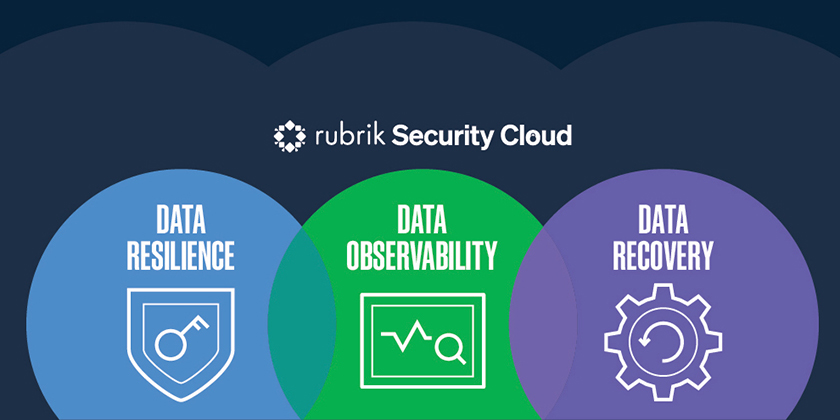
As the pioneer of Zero Trust Data Security, Rubrik’s approach focuses on three key pillars – Data Resilience, Data Observability, and Data Recovery.
- Data Resilience – this is the most fundamental component of Data Security as it ensures that if an attacker breaches the organisation, they’re unable to cause significant damage. In essence, data resilience means data is always available to the right user on the right platform at the right time for the right duration. At its core, this involves safeguarding data with secure backups so they can never be deleted, compromised, or encrypted. As a result, these data copies are always available for rapid recovery following an attack.
- Data Observability – the main goal of any attack is to compromise data, whether through encryption, exfiltration, or destruction. By continuously scanning backup data over time, you can pinpoint when, where, and how attacks have impacted systems so compromises can be remediated quickly. Rubrik’s Data Observability Engine includes pre-built scanners for sensitive data discovery, blast radius identification, and threat hunting, turning backup data into an active weapon of cyber defence.
- Data Recovery – once an attack has occurred, quarantining malware and avoiding reinfection during the recovery process is absolutely critical. With automated backups and machine-learning algorithms to identify the most up-to-date clean data copies, enterprises can simply turn back the clock on any ransomware attack and recover from a point-in-time immediately prior with minimal data loss.
Today, protecting your business requires security at the point of data.
With these three pillars in place, organisations can be confident their data is available, has integrity, and can be trusted when it’s needed the most. This is the future of cyber security – because if your data is secure, your business is secure.
To learn more about Zero Trust Data Security, join Rubrik on August 16 for its Data Security Talks event. Speakers include Craig Jones, Director of Cybercrime at Interpol, Michael Mestrovich, former CIA CISO and Rubrik CISO, and more. For more information, or to register, visit the Data Security Talks event page.
Organizations rely on Rubrik for resilience against cyber attacks and operational disruptions with automation, fast...