The notorious ransomware collective Conti compromised more than 40 companies worldwide in an attack that took three days, according to Group-IB's report titled CONTI ARMADA: ARMATTACK CAMPAIGN.
In two years, Group-IB observed the ransomware operators attacked more than 850 victims including corporations, government agencies, and even a whole country.
According to Group-IB, Conti is considered one of the most successful ransomware groups. The gang's existence first appeared on the radar in February 2020, when malicious files with the extension “.сonti” began to appear. However, Group-IB researchers believe the initial test versions of the malware date back to November 2019.
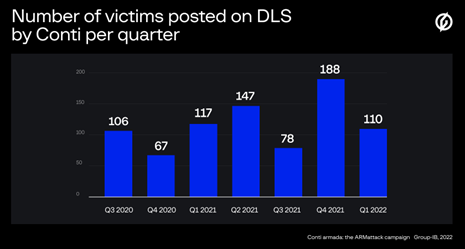
Conti has dominated the ransomware scene in terms of the number of companies whose data has been encrypted. In 2020, Conti published data belonging to 173 victims on their dedicated leak site (DLS). By the end of 2021, Conti came out on top as one of the largest and most aggressive groups, having published data belonging to 530 companies on its DLS.
A few months into 2022, the group posted information belonging to 156 companies, making for a total of 859 DLS victims in two years, including 46 in April 2022. In the same month, Conti’s "cyber war" against Costa Rica in April 2022 led to a state of emergency being declared. According to Group-IB, the actual number of victims is believed to be significantly higher.
According to Ivan Pisarev, head of dynamic malware analysis team at Group-IB's threat intelligence department, Conti's increased activity and the data leak suggest that ransomware is no longer a game between average malware developers, but an illicit RaaS industry that gives jobs to hundreds of cyber criminals worldwide with various specialisations.
"In this industry, Conti is a notorious player that has in fact created an 'IT company' whose goal is to extort large sums.
"It is difficult to predict what will happen to Conti in the future: whether it will continue working after a large-scale rebranding or be divided into smaller sub-projects.
"It is clear, however, that the group will continue its operations, either on its own or with the help of its 'subsidiary' projects," Pisarev said.
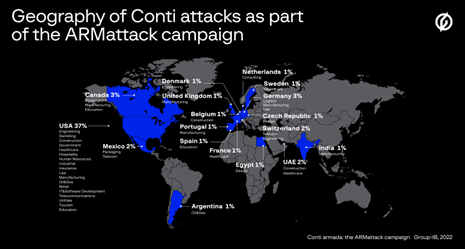
Conti and their affiliates attack often and quickly according to Group-IB experts, after analysing one of the group's lightning-fast and most productive campaigns, codenamed "ARMattack". The campaign lasted about a month (from 17 November to 20 December 2021), but it turned out to be extremely effective. Group-IB researchers observed the attackers compromised more than 40 organisations worldwide. Most attacks were carried out in the US (37 per cent), but the campaign also surged through Europe, with victims in Germany (3 per cent), Switzerland (2 per cent), the Netherlands, Spain, France, the Czech Republic, Sweden, and Denmark (1 per cent each). The group even attacked organisations in the UAE (2 per cent) and India (1 per cent).
The top five industries most frequently targeted by Conti are manufacturing (14%), real estate (11.1%), logistics (8.2%), professional services (7.1%), and trade (5.5%). After gaining access to a company's infrastructure, the threat actors exfiltrate specific documents (most often to determine what organisation they are dealing with) and look for files containing passwords (both plaintext and encrypted). After acquiring all the necessary privileges and gaining access to all the devices they are interested in, the hackers deploy ransomware to all the devices and run it.
Group-IB Threat Intelligence team added that the gang's fastest attack took three days from initial access to data encryption, after analysing Conti’s 'working hours.' It is likely the group members are located in different time zones. On average, according to Group-IB researchers, Conti "works" 14 hours a day without holidays (except for New Year holidays) and weekends. Group-IB has also observed the group starts working closer to noon (GMT+3) and its activity declines only after 9:00 PM.
Conti has worked closely with other ransomware operators such as Ryuk, Netwalker, LockBit, and Maze. The group tested Maze's ransomware, reverse-engineered it, and thereby significantly improved their own. An analysis of the ARMattack campaign revealed that the group’s arsenal included not only previously described Windows tools, but also Linux ransomware: Conti and Hive.
Group-IB observed that Conti tends to create unique tools without reusing code snippets, the code for their tools are designed to avoid being identified or linked to common patterns. Before the chat logs were leaked, cyber security researchers could only assume that some RaaS (Ransomware-as-a-service) affiliate programs were in fact Conti divisions.
The chat logs revealed extensive interactions. Sometimes Conti used network access from other initial access brokers, and other times, it appeared the gang shared their own access for a modest 20% of the revenue. Like a legitimate IT business, Group-IB researchers continued, Conti has its own HR, R&D, and OSINT departments with team leads, regular salary payments, and an incentive program.
One of Conti’s distinctive features is using new vulnerabilities, which helps the group gain initial access. Group-IB observed Conti exploiting the recent CVE-2021-44228, CVE-2021-45046 and CVE-2021-45105 vulnerabilities in the log4j module. Conti then exploited these vulnerabilities to attack vCenter servers.
The group monitors fresh vulnerabilities carefully, according to the leaked chat logs. One of the tasks from Conti’s CEO to the technical team was to monitor Windows updates and analyse changes made with new patches. The Conti crew also includes specialists with experience in discovering zero-days.
The geography of Conti's attacks is vast but does not include Russia. The group seems to adhere to the unspoken rule among Russian-speaking cybercriminals: 'do not attack Russian companies.' Most attacks occur in the United States (58.4%), followed by Canada (7%), the United Kingdom (6.6%), Germany (5.8%), France (3.9%), and Italy (3.1%).
Another reason behind not targeting Russian companies is that key Conti members refer to themselves as 'patriots.' According to Group-IB, this could have been behind the cause of an 'internal conflict' within the group in February 2022, which resulted in some of Conti's information being leaked online. The published data included private chat logs, the servers they use, a list of victims, and details of Bitcoin wallets, which stored over 65,000 BTC in total. The leaked chats revealed that the group had faced serious financial difficulties and that their boss had gone off the radar, but its embers were fully prepared to restart the project after 2 to 3 months.
[Related: Chinese hackers spying undetected, leveraging ransomware as a diversion]

