Sophos explains in detail how both operators gained access to the network through an unpatched Microsoft Exchange Server, but then used different tactics to implement their attacks in the article, Conti and Karma Actors Attack Healthcare Provider at Same Time Through ProxyShell Exploits.
Across the estimated timeline, there was a period of around four days when the Conti and Karma attackers were simultaneously active in the target’s network, moving around each other, downloading and running scripts, installing Cobalt Strike beacons, collecting and exfiltrating data, and more, according to Sean Gallagher, senior threat researcher at Sophos.
“To be hit by a dual ransomware attack is a nightmare scenario for any organisation.
“Karma deployed the final stage of its attack first, dropping an extortion notice on computers demanding a bitcoin payment in exchange for not publishing stolen data.
“Then Conti struck, encrypting the target’s data in a more traditional ransomware attack. In a strange twist, the Conti ransomware encrypted Karma’s extortion notes,” Gallagher said.
The dual attack
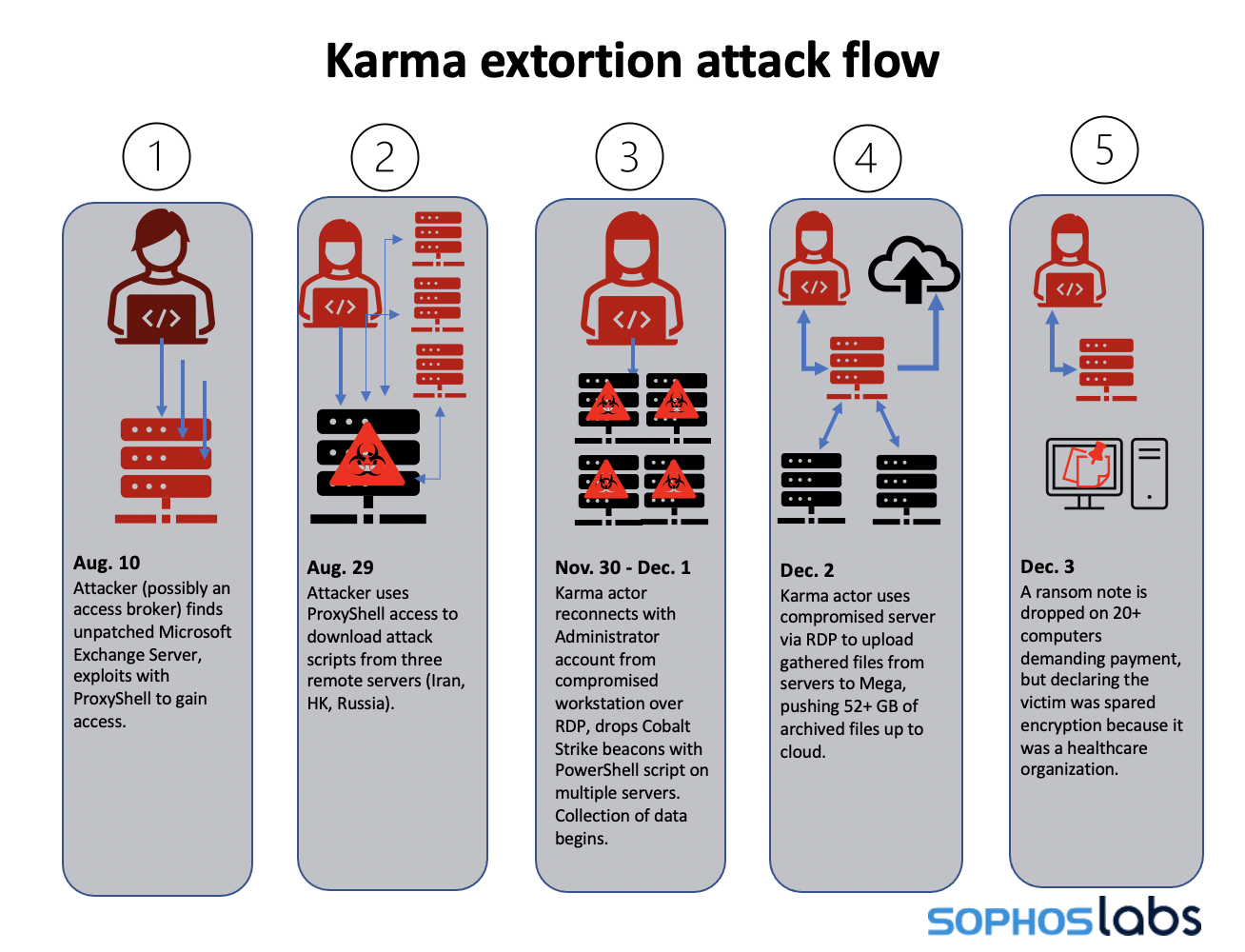
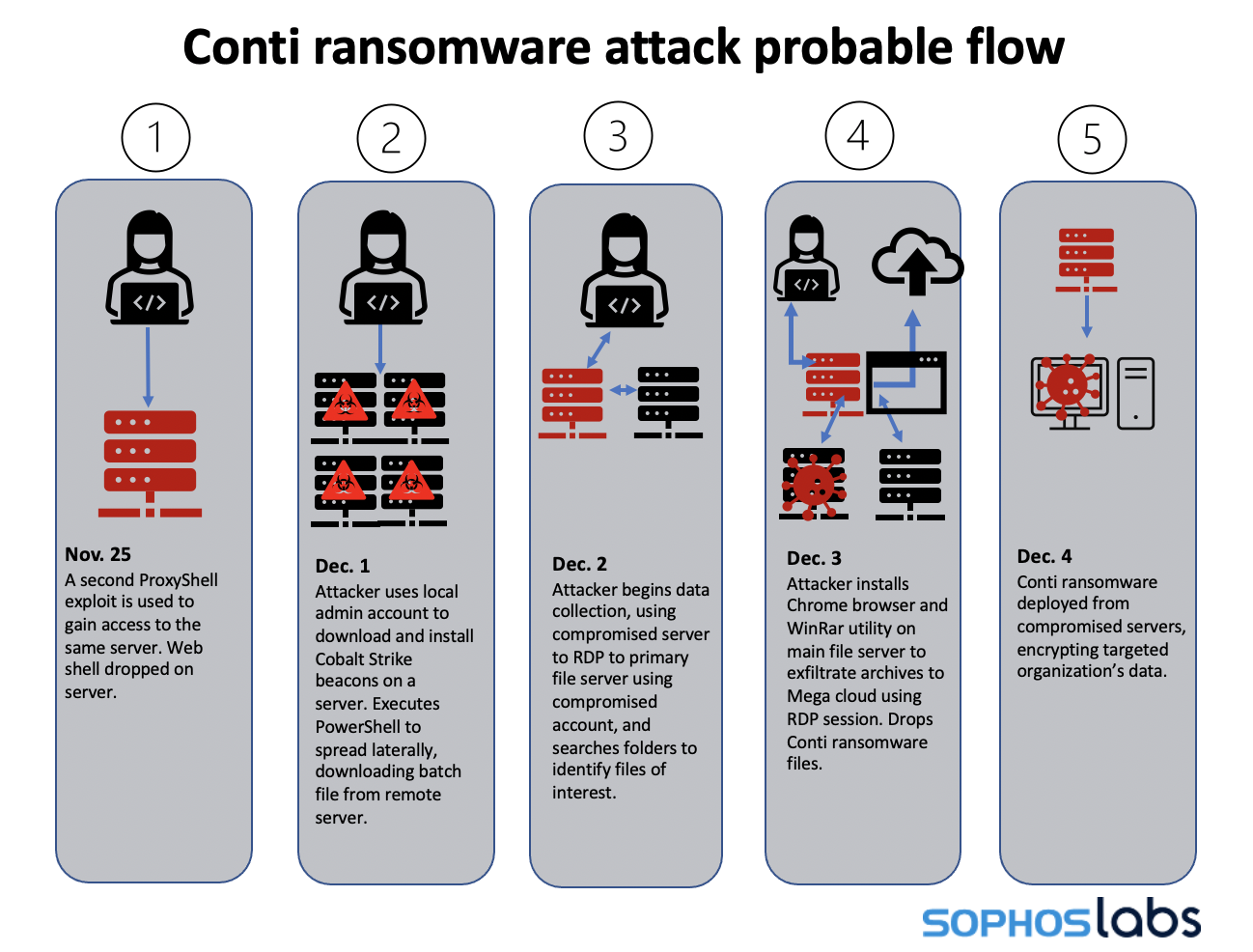
Sophos researchers believe that the first incident started on 10 August 2021, when attackers, possibly initial access brokers, used a ProxyShell exploit to gain access to the network and establish a foothold on the compromised server. The Sophos investigation showed that almost four months passed before Karma appeared on 30 November 2021, and exfiltrated more than 52 gigabytes of data to the cloud.
On 3 December 2021, three things happened:
- The Karma attackers dropped an extortion note on 20 computers, demanding a ransom and explaining that they did not encrypt the data because the target was a healthcare provider.
- Conti was quietly operating in the background, also exfiltrating data.
- The target started onboarding Sophos’ incident response team to help with Karma.
While Sophos was onboarding, Conti deployed its ransomware on 4 December 2021. Sophos subsequently tracked the start of the Conti attack to another ProxyShell exploit leveraged on 25 November 2021.
Gallagher added that Sophos analysts have seen several cases recently where ransomware affiliates, including affiliates of Conti, used ProxyShell exploits to penetrate the target’s networks.
“We have also seen examples of multiple actors exploiting the same vulnerability to gain access to a victim.
“However, very few of those cases involved two ransomware groups simultaneously attacking a target and it shows, literally, how crowded and competitive the ransomware landscape has become,” Gallagher said.
Whether the initial access broker sold access to two different ransomware affiliates, or whether the vulnerable exchange server was just an unlucky target for multiple ransomware operators, the fact that a dual attack was possible is a powerful reminder to patch widely known, internet-facing vulnerabilities at the earliest opportunity, Gallagher further explained.
“Defence-in-depth is vital for identifying and blocking attackers at any stage of the attack chain, while proactive, human-led threat hunting should investigate all potentially suspicious behaviour, such as unexpected remote access service logins or the use of legitimate tools outside the normal pattern, as these could be early warning signs of an imminent ransomware attack,” Gallagher explained.
[Related: Ransomware attack techniques now span the entire kill chain]

