In contrast, only 27 per cent of applications were vulnerable to one serious exploitable vulnerability every 30 days or less. This means that as an attacker, it won't take much effort before coming across a vulnerable site, that if exploited, could lead directly to the attacker gaining control of the system, or to the direct exfiltration of internal information.
According to PwC's 2022 Global Digital Trust Insights Survey, business leaders are beginning to create a blueprint for the securable enterprise. Throughout the pandemic, the cloud has become a "must-have", not just a "nice-to-have", and cloud security is expected to posture management to follow the same trajectory. This evolution is expected as more business' critical and sensitive data becomes stored in the cloud – while in parallel, organisations look to reduce the business and operational risk of a breach to their business.
Gartner predicts that by 2025, 99 per cent of cloud security failures will be the client’s fault. Cloud security posture management is increasingly important, as is a clear understanding of the shared responsibility model (SRM) to mitigate the cyber security risks of cloud computing.
What is cloud security posture management?
Cloud security posture management (CSPM) allows for the more seamless management of cloud security.
CSPM is a relatively new class of tools, but as businesses increase the use of the cloud and continuously adjust the make-up and mixture of cloud services they consume, CSPMs help to ensure you:
- Have visibility across your cloud assets
- Can configure your cloud infrastructure correctly and consistently
- Can manage user access rights and entitlements with ease
- Can respond and remediate any issues as quickly as possible (often as an automated process)
- Can evaluate the effectiveness of your security, benchmarked against key industry standards
- Are meeting your data security obligations
- Can generate consolidated operational and business reports.
As business consumption of cloud services scales across one or more providers, CSPM tools offer the means to improve threat or risk visibility, reduce complexity, minimise the risk of breach due to misconfigurations and provide the means to evaluate and demonstrate the effectiveness of your security and data privacy efforts.
Cloud security: whose responsibility is it?
To fully realise the benefits of a CSPM, it’s fundamental that businesses understand the SRM. In short, the SRM refers to the fact that cloud security providers (CSPs) and cloud service customers have distinct responsibilities to ensure the cloud is secure and compliant – the shared responsibility model helps to make that clear.
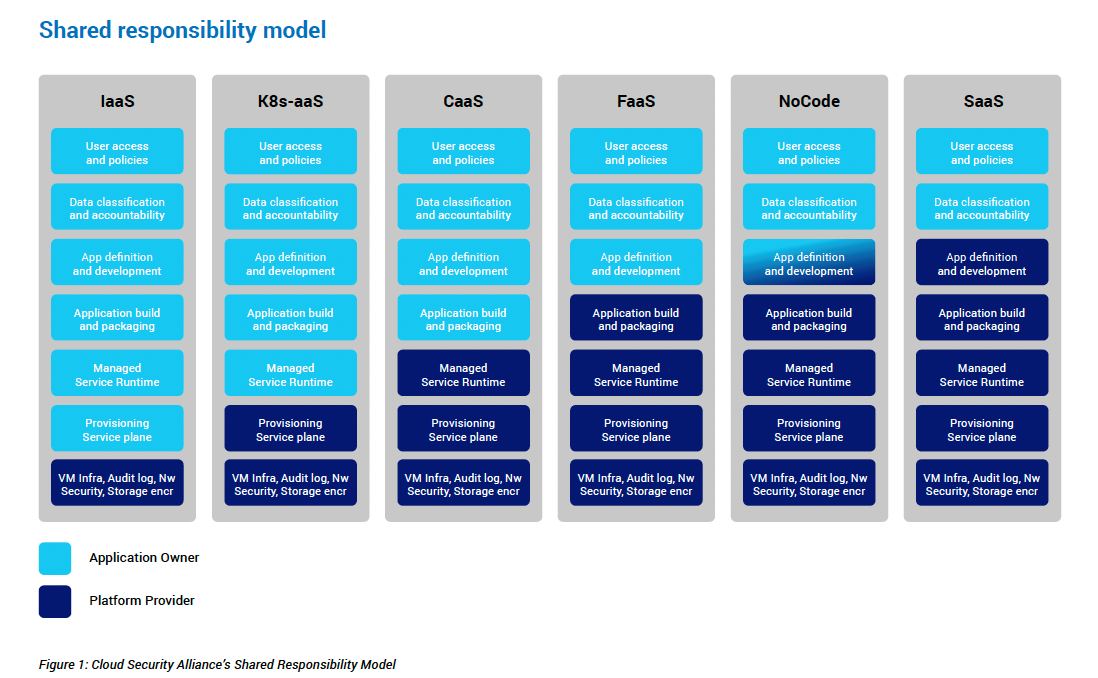
This is a useful high-level framework for understanding and learning about the division of responsibility. It’s also critical to validate this framework against those provided by the service providers themselves.
Amazon Web Services, Microsoft Azure, Google Cloud Platform and other providers have clearly defined their views on the shared responsibility model. There are subtle but critical differences between them all. Public cloud providers have no choice but to take their security and compliance responsibilities seriously.
Still, they need to draw a line over how far it is reasonable for them to go to perform basic security functions, monitor and ensure compliance on behalf of their service consumers.
This makes sense as CSPs can’t control everything users do in their cloud. Likewise, users can’t expect to control the security across the CSPs’ servers and networks. The SRM helps to ensure that both parties are aware of the rules and take ownership for securing the resources they control.
Unfortunately, the shared responsibility model is not well understood and studied by businesses – consumers of cloud services. CSPs understand the SRM better. Hence Gartner’s bold predictions about where the fault for breaches will lie in 2025.
It can be confusing, but the SRM helps understand shared responsibility since it varies across IaaS, SaaS and PaaS, which are different, as shown in Figure 1.
Clear, understood, and well-defined roles on security are critical to security risk management in any enterprise. Cloud risk management may be even more critical to the success of the business blueprint. Having a clear understanding of the shared responsibility model will also help ensure that there’s less finger pointing in the event of a breach. More importantly, it can ensure there is good security in place across the entire threat surface, cloud environment and local data security obligations.
The role of CSPM in the future
CSPM helps to ensure visibility across assets as well as security tools and controls, and that both parties are holding up their part of the shared responsibility.
There are many third-party providers offering CSPM tools today. There is still tremendous potential for innovation, especially in CSPM-as-a-Service that can provide integrated visibility across multiple major cloud service providers to truly deliver on the promise of reducing complexity.
It would also be tremendously valuable for CSPM vendors to invest in and enrich their identity protection and monitoring capabilities. User access entitlements and permissions in the cloud are increasingly broad and detailed, and traditional identity and access management tools struggle to keep up with the complexity.
Businesses would greatly benefit from cloud infrastructure entitlement management (CIEM) as a "specialised identity centric solution" as part of their CSPM solution. CIEMs can inventory people and non-people identities, determine what they can and can’t access, as well as what they have permissions to do with that data.
However, the real value is that they can do it at the scale, speed, granularity and agility of the dynamic multi and hybrid environments that businesses operate in today.
The importance of CSPM will only increase in coming years as businesses move towards increasingly cloud-based, identity-driven and data-centric approaches that support remote working, adopt zero-trust and SASE models. The greatest cyber security risk to businesses remains lack of visibility, and CSPMs are promising a front row seat.
[Related: China suspected of cyber attack on News Corp]

