Banking Trojans allow cyber criminals to steal money from people’s online banking accounts or digital wallets and can deploy ransomware on victims’ devices, making them one of the most dangerous types of malware.
Kaspersky researchers spotted a new function in QakBot’s recent version – the ability to steal emails from the attacked machine, which are then used in social engineering campaigns targeting those people on the victim’s email contact list.
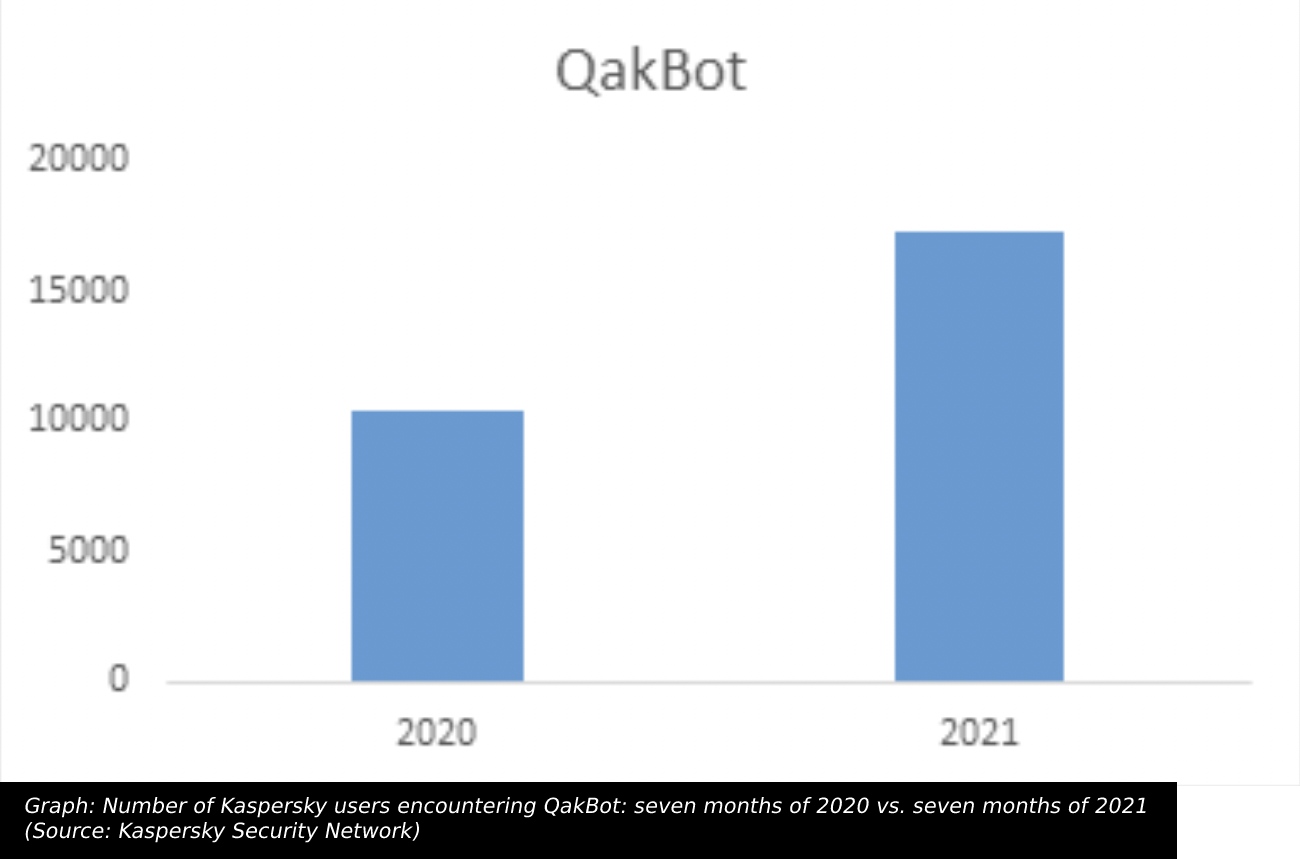
This particular Trojan has been around since 2007 and has become one of the most powerful existing banking malwares.
New elements found in the latest iteration of QakBot include being able to detect if the victim has an antivirus software installed in the device, the capability to protect itself from being analysed and debugged by experts or automated tools.
According to Noushin Shabab, senior security researcher at Kaspersky, QakBot is unlikely to stop its activity anytime soon.
“The threat actors behind it keep adding new capabilities and updating its modules to maximise the revenue impact, along with stealing details and information."
Recently, QakBot has been actively spread via the Emotet botnet. While this botnet was taken down at the beginning of the year, the infection attempt statistics show the actors behind QakBot have found a new way of propagating this malicious software," Shabab added.
Kaspersky recommended the following to stay safe from financial threats like QakBot:
- Use the multifactor authentication option on your online banking;
- Keep your apps and operating system updated – as attackers exploit loopholes in widely used programs to gain entry to your device; and
- Don’t click on links or open documents from spam messages,
This particular Trojan has been around since 2007 and has become one of the most powerful existing banking malwares that has evolved beyond capabilities that are usually found in banking malware.
[Related: Defence opens applications for ADF Cyber Gap Program]

