Epworth HealthCare, which operates several locations throughout Melbourne and Geelong, has found itself at the centre of another alleged data breach after the 0APT ransomware group claimed to have stolen almost a terabyte of data.
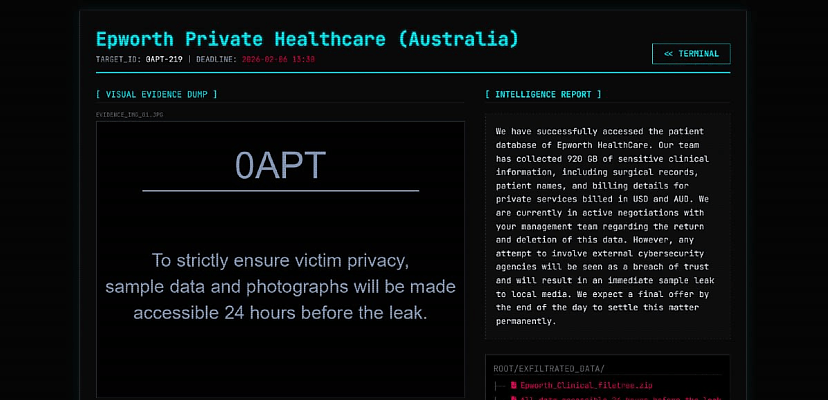
“We have successfully accessed the patient database of Epworth HealthCare,” the hackers said in a February leak post.
“Our team has collected 920 GB of sensitive clinical information, including surgical records, patient names, and billing details for private services billed in USD and AUD.”
0APT said it was actively negotiating with Epworth, and warned the healthcare provider not to bring in external parties.
“Any attempt to involve external cybersecurity agencies will be seen as a breach of trust and will result in an immediate sample leak to local media,” the hacker said.
“We expect a final offer by the end of the day to settle this matter permanently.”
0APT has not listed a ransom demand, nor published any evidence of a successful hack (aside from a file tree that Cyber Daily has been unable to access), but has said it will publish the data on 6 February.
However, Epworth HealthCare has said it has found no evidence of any data breach.
“Epworth HealthCare is aware of an unverified report suggesting that some data held by our organisation may have been compromised. The allegation forms part of a broad global report that references multiple organisations,” an Epworth spokesperson told Cyber Daily.
Epworth HealthCare is one of dozens of victims listed recently by 0APT.
“Currently, there is no verified evidence of any impact to our systems or data, and our services remain secure. Irrespective, we have activated our extensive cyber incident response protocols immediately,” the spokesperson said.
Epworth HealthCare said it takes data integrity seriously and that it had engaged specialist partners who have found no indicators of compromise.
“Patient care across all Epworth hospitals remains fully operational and safe,” the spokesperson said.
Who is 0APT?
0APT only emerged this year, sharing details of its first tranche of victims on 28 January. Since then, it appears to have been quite active, sharing the details of almost 100 victims in about one week.
The group claims to be a ransomware-as-a-service operation that describes itself as a “politically neutral underground syndicate”.
“We do not want to destroy your business, we only want financial compensation. Treat this as a sudden tax on your security negligence,” the group said on its darknet leak site.
It is also actively recruiting affiliates and pentesters, saying: “We provide the locker, chat support, and negotiation. You bring the target. We offer maximum % split on every payment.”
Analysts, however, are divided as to the group’s authenticity.
On the one hand, cyber security firm Red Piranha featured a detailed breakdown of 0APT’s operations in one of its most recent Threat Intelligence reports. It described the group’s malware as a “crypto-ransomware strain written in C# targeting Windows environments with cross-platform capabilities”.
“Analysis reveals the malware uses a hybrid encryption scheme combining Salsa20 stream cipher for file encryption with RSA-1024 for key protection. This differs from the AES-256 claim in ransom notes – a simplification for victims,” Red Piranha said.
“The code shares technical fingerprints with Haron ransomware (2021), including the unusual trait of not appending extensions to encrypted files.”
On the other hand, while Red Piranha takes the group’s activity seriously, open-source threat intelligence tracker Ransomware.live is less convinced that the group is engaging in actual ransomware attacks.
“The group appears unreliable,” Ransomware.live said in its entry for 0APT.
“Most, if not all, of its alleged victims cannot be verified and appear to be randomly selected organisations. WE HAVE DECIDED TO REMOVE ENTRIES FOR THIS GROUP.”
For its part, 0APT appears to have published data belonging to several of its victims. However, due to its leak site’s infrastructure – or perhaps because the data does not actually exist – Cyber Daily has been unable to download any sample data to verify the group’s claims.
Who is the victim
Epworth HealthCare is Victoria’s largest not-for-profit healthcare provider, employing more than 8,000 staff and treating more than 230,000 patients in the 2023–24 period.
The provider was implicated in a ransomware incident last year, when the Global ransomware group claimed to have stolen 40 gigabytes of data. However, Epworth HealthCare said at the time that its own systems were secure and that the incident related to an unnamed third party.
“Epworth HealthCare has completed a thorough investigation – supported by independent cyber security specialists – into claims made yesterday afternoon on the dark web alleging an IT compromise,” Epworth HealthCare told Cyber Daily at the time.
“We can confirm that Epworth’s IT systems have not been breached or compromised. No data stored within Epworth’s IT environments has been accessed, lost or altered, patient care remains fully operational and safe across all Epworth hospitals [and] investigations indicate the claims may relate to a third party that is not connected to Epworth’s IT environment. The third party has been notified.”

David Hollingworth
David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.