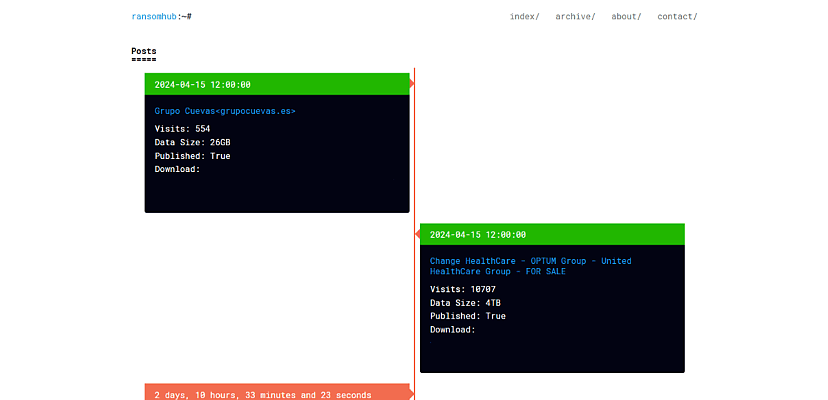
RansomHub, the second ransomware gang to list data belonging to the UnitedHealth subsidiary taken from an attack earlier this year, announced that the data is now available for purchase, having only yesterday (16 April) posted a sample of the data.
“The data is now for sale. Anyone interested in the purchase should contact RansomHub,” said the threat group.
Interestingly, as reported yesterday by Cyber Daily, RansomHub had initiated a countdown for the release and/or sale of Change Healthcare data, and at the time of the sale listing, the countdown still had roughly four days left.
RansomHub has reiterated that the stolen data belongs to “tens of insurance companies, including and not limited to Medicare, Tricare, CVS-CareMark, Loomis, Davis Vision, Heath Net, MetLife, Teachers Health Trust and tens of [other] insurance companies”.
Additionally, this data includes medical records, dental records, claims information, payment information, and the personally identifiable information (PII) of both patients and active US military and navy personnel, including phone numbers, addresses, social security numbers, emails and more, over 3,000 source code files, insurance records and “many more.”
“Change Health[care] and UnitedHealth processing of sensitive data for all of these companies is just something unbelievable,” added RansomHub.
“For most US individuals out there doubting us, we probably have your personal data.”
Interestingly, in what appears to be a last-ditch effort, RansomHub has made a call out to the affected insurance companies, letting them know that they can have their data removed from the total sale data if they “contact” the threat group, which likely means negotiate a ransom.
“Affected insurance providers can contact us to prevent leaking of their own data and removing from the sale.”
RansomHub’s new listing comes only a day after the group posted a sample of the exfiltrated Change Healthcare data, taunting the healthcare provider by advertising the data to other threat actors.
“Before our final reveal, below you will find attached screenshots of just a mere sample of data we have,” said RansomHub.
“It is just unbelievable the amount and sensitivity of data that Change Healthcare was in possession of.
“If Change Healthcare / United Health don’t care about your data, maybe you should ...”
This cyber incident has been a major saga for UnitedHealth and Change Healthcare, with the company having already paid a ransom to the previous threat group that claimed responsibility for the attack, ALPHV.
ALPHV received a US$22 million ransom payment, only to disband and run away with the money, leaving the ransomware affiliate “Notchy” and Change Healthcare without what they were promised.

Daniel Croft