Proofpoint observed COVID-19 themes impacting education institutions throughout the pandemic, but consistent, targeted credential theft campaigns using such lures targeting universities began in October 2021. Following the announcement of the new Omicron variant in late November, the threat actors began leveraging the new variant in credential theft campaigns.
Threat actors continue to use COVID-19-themed lures in campaigns targeting multiple industries and geographic areas, with the threats specifically targeting universities, which is interesting due to the specificity in targeting and effort to mimic legitimate login portals.
Proofpoint researchers have noted that this activity will likely increase in the next two months as colleges and universities provide and require testing for students, faculty and other workers traveling to and from campus during and after the holiday season, and as the Omicron variant emerges more widely.
The threat actors will adopt COVID-19 themes given the introduction of the Omicron variant, the Proofpoint researchers added.
This assessment is based on previously published research that identified COVID-19 themes making a resurgence in email campaigns following the emergence of the Delta variant in August 2021.
Campaign Details
The COVID-19-themed campaigns including the Omicron variant lures include thousands of messages targeted to dozens of universities in the US.
The phishing emails contain attachments or URLs for pages intended to harvest credentials for university accounts, and the landing pages typically imitate the university’s official login portal, although some campaigns feature generic Office 365 login portals, the Proofpoint researchers have found.
In some cases, such as the Omicron variant lures, victims are redirected to a legitimate university communication after credentials are harvested.
Proofpoint researchers have observed this threat actor pivot from Delta variant-themed email lures to Omicron themes following the announcement of the new variant.
Emails with URLs use subjects such as "Attention Required - Information Regarding COVID-19 Omicron Variant - November 29", with a link to a spoofed landing page such as:
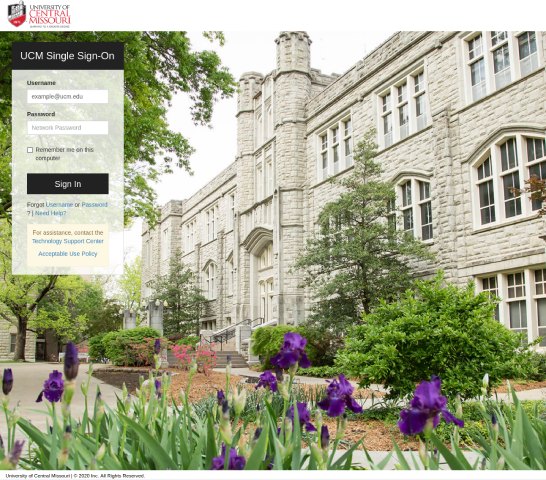
Messages distributing attachments included subject lines such as “COVID Test”.

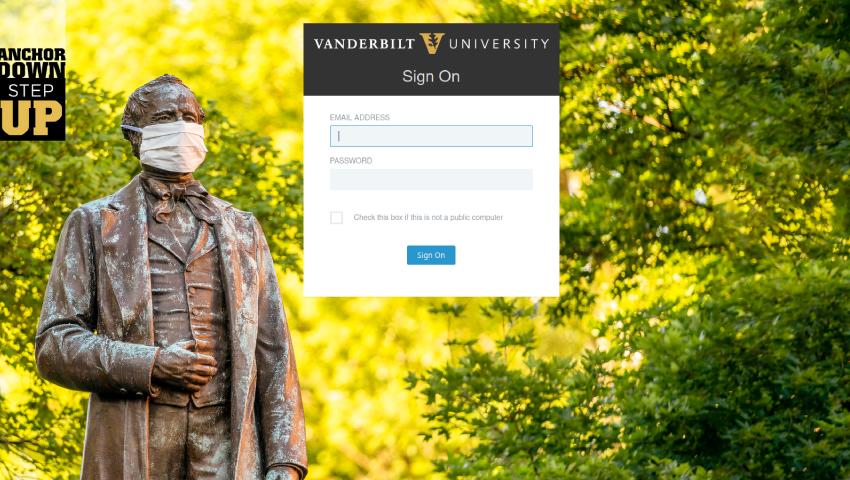
Proofpoint researchers have identified multiple threat clusters using COVID-19 themes to target universities using different tactics, techniques and procedures (TTPs).
In addition to multiple delivery methods – Proofpoint researchers have also observed both URL and attachments in campaigns – activity clusters use different sender and hosting methods to distribute credential theft campaigns.
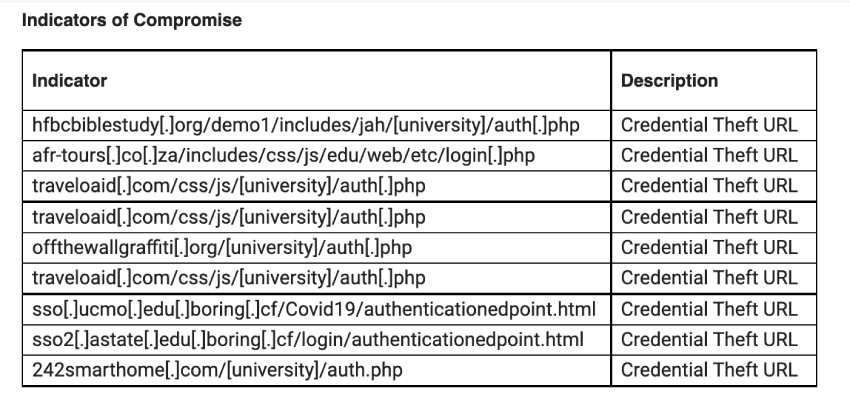
In the Omicron variant campaign, threat actors leverage actor-controlled infrastructure to host credential theft webpages using similar domain naming patterns.
These include:
- sso[.]ucmo[.]edu[.]boring[.]cf/Covid19/authenticationedpoint.html
- sso2[.]astate[.]edu[.]boring[.]cf/login/authenticationedpoint.html
Attachment-based campaigns have leveraged legitimate but compromised WordPress websites to host credential capture webpages, including:
- hfbcbiblestudy[.]org/demo1/includes/jah/[university]/auth[.]php
- afr-tours[.]co[.]za/includes/css/js/edu/web/etc/login[.]php
- traveloaid[.]com/css/js/[university]/auth[.]php
In some campaigns, threat actors attempted to steal multifactor authentication (MFA) credentials, spoofing MFA providers such as Duo.
Stealing MFA tokens enables the attacker to bypass the second layer of security designed to keep out threat actors who already know a victim’s username and password.
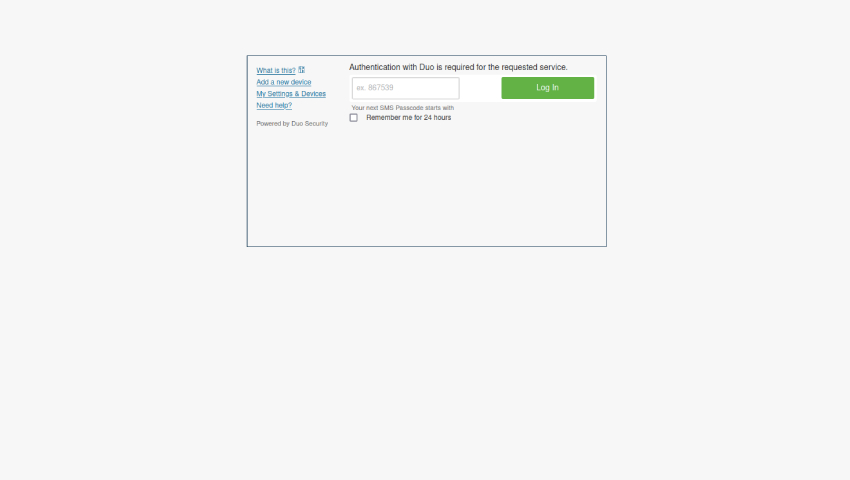
While many messages are sent via spoofed senders, Proofpoint researchers have observed threat actors leveraging legitimate, compromised university accounts to send COVID-19 themed threats. It is likely the threat actors are stealing credentials from universities and using compromised mailboxes to send the same threats to other universities.
Proofpoint does not attribute this activity to a known actor or threat group, and the ultimate objective of the threat actors is currently unknown.
[Related: Chinese cyber criminals target Australian power grid]

Nastasha Tupas
Nastasha is a Journalist at Momentum Media, she reports extensively across veterans affairs, cyber security and geopolitics in the Indo-Pacific. She is a co-author of a book titled The Stories Women Journalists Tell, published by Penguin Random House. Previously, she was a Content Producer at Verizon Media, a Digital Producer for Yahoo! and Channel 7, a Digital Journalist at Sky News Australia, as well as a Website Manager and Digital Producer at SBS Australia. Nastasha started her career in media as a Video Producer and Digital News Presenter at News Corp Australia.

