A multi-year campaign by an Iranian hacking group considered to be linked to the Islamic Revolutionary Guard Corps (IRGC) to hack the computer of a defence contractor was uncovered by cyber security company Proofpoint this week.
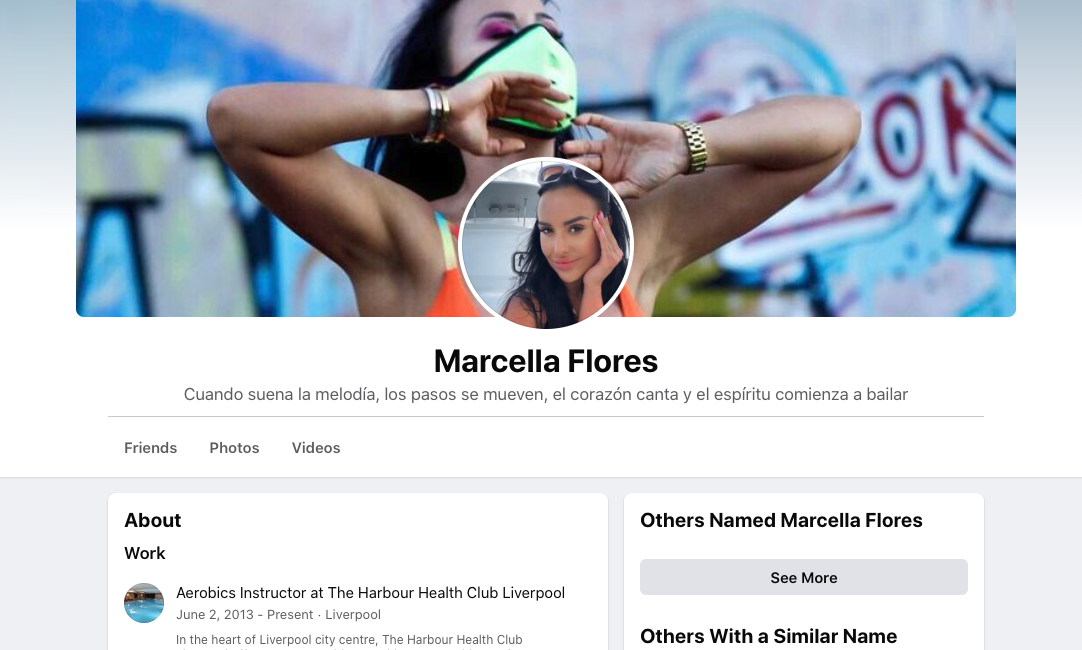
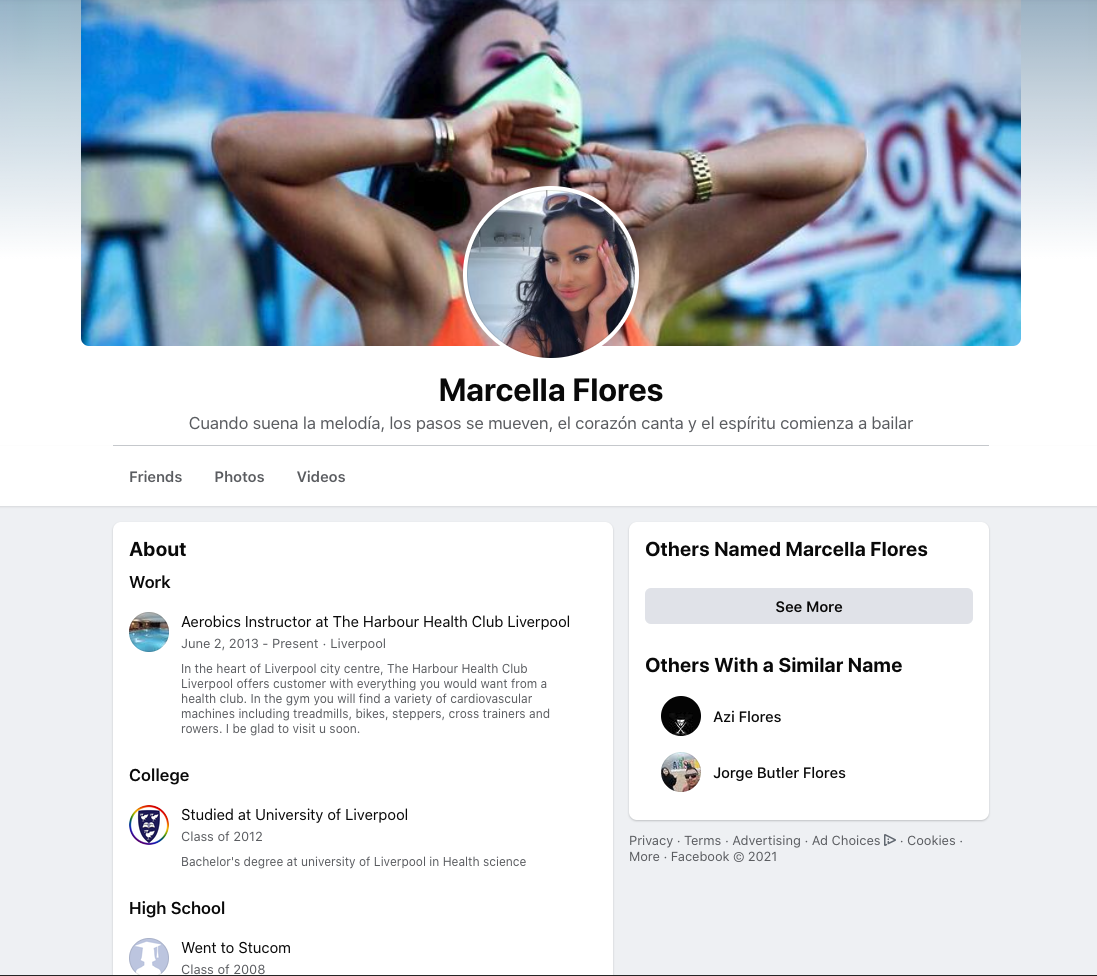
Carefully crafting the character Marcela (Marcy) Flores, the hackers added their target as a friend on Facebook in late 2019 before kickstarting their online friendship by exchanging messages in November of the following year. The cyber criminals finally struck in June 2021, attempting to infect the target's computer with malware via an email.
The target works as a defence contractor in the aerospace industry in the US.
According to the carefully crafted profile, Flores was an aerobics instructor at the Harbour Health Club in Liverpool, UK, and graduated from the University of Liverpool in 2012.
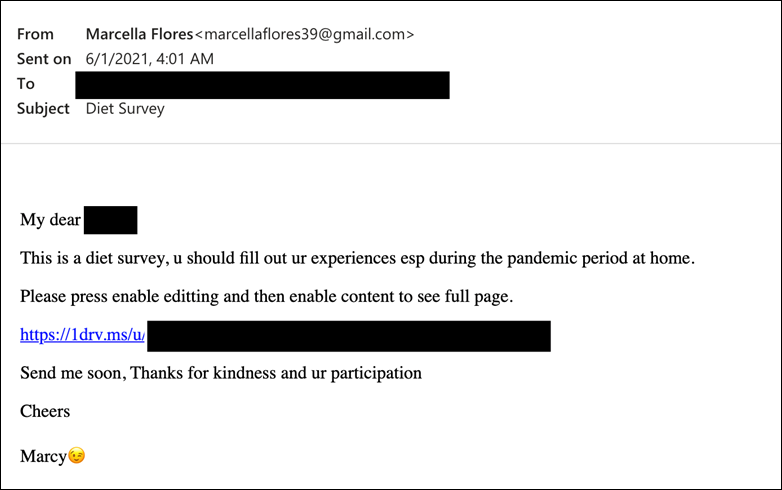
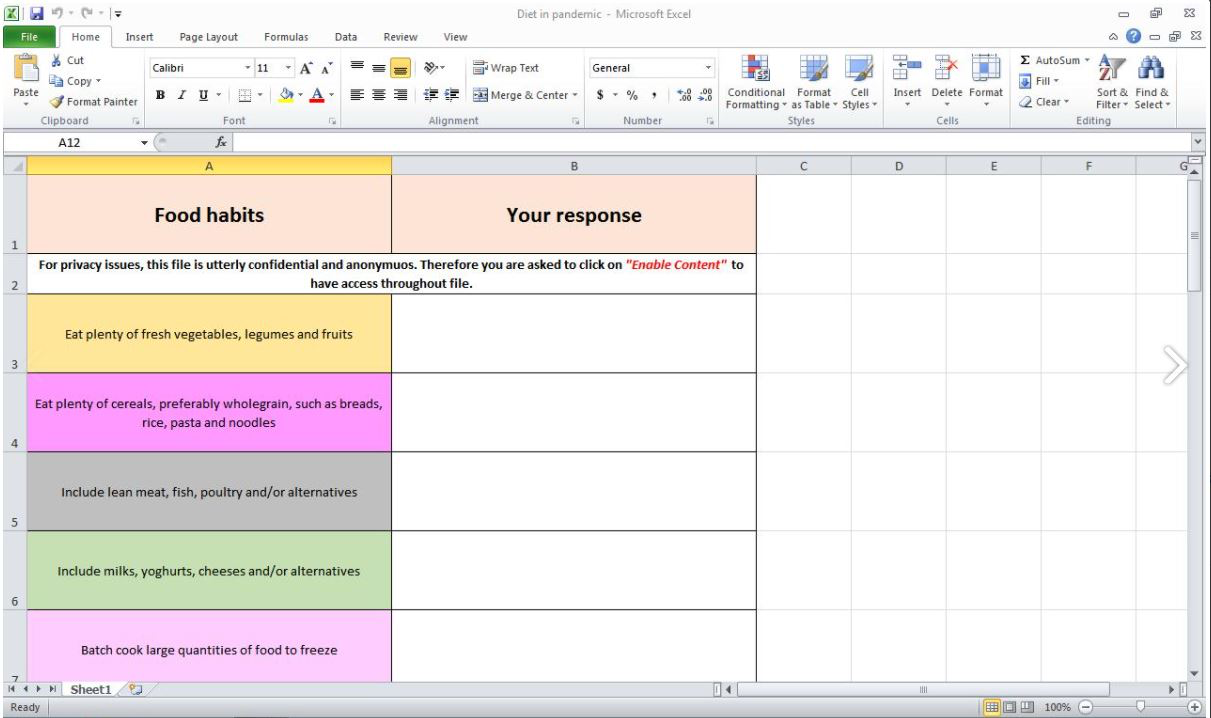
Having established their online relationship, the malicious actor sent their online beau an email with a link to a food diary to make sure that the contractor was staying healthy amid the COVID-19 pandemic. Proofpoint found that clicking on the link opened up an Excel spreadsheet titled "Diet in pandemic", but also downloaded a .rar file that installed a reconnaissance tool closely mirroring those used by Iranian threat actors.
According to Proofpoint, the malware (dubbed "LEMPO") was developed for long-term data collection from the target while camouflaging its presence by deleting all traces of the crime.
Despite the multi-year campaign from the hackers, the contractor wasn’t the ultimate target of the malware. According to Proofpoint, malicious actors regularly target smaller and more penetrable companies in order to infect upstream targets later on, thereby collecting more critical information.
The recent discovery comes after a concerted campaign by Iranian backed cyber groups to honeypot people online. Earlier this month, Facebook banned some 200 profiles of hacking group Tortoiseshell, which had been targeting defence and aerospace companies across the US, Europe and the UK.
Proofpoint believes that the malicious actors, dubbed TA456, were co-ordinated by Iranian company Mahak Rayan Afraz (MRZ), which has known links to the Islamic Revolutionary Guard Corps.
Sherrod DeGrippo, senior director threat research and detection at Proofpoint, explained how the cyber criminals operate.
“Proofpoint routinely detects TA456 campaigns attempting to conduct reconnaissance against customers in the defence industry, specifically those involved in aerospace engineering. In the just the past six months, TA456 has used the following themes in their reconnaissance e-mails; Career Focused, COVID-19 News, Political News,” DeGrippo explained.
“TA456 reconnaissance emails typically contain a number of personalised links along with a tracking pixel hosted on an actor controlled website. TA456 then uses relationships cultivated on social media like Facebook to deploy malware onto sensitive networks. The malware, dubbed LEMPO by Proofpoint, is a VBS implant dropped by an .xlsm. The VBS implant conducts reconnaissance and profiling of the machine and exfiltrates the data to an actor controlled email account.
“Proofpoint assesses TA456 currently conducts cyber operations in support of Iranian espionage efforts. While Proofpoint did not observe any remote access trojans or C2 channels in this incident, the information gathered by the VBS implant could be operationalised in a variety of ways including the utilisation of stolen VPN credentials, exploitation of vulnerabilities in the identified software, or the customisation of follow on malware to be delivered.
“Operationally, TA456 is aligned with Iranian government espionage collections. Phishing targets almost all work in the defence industrial base, often supporting US efforts in the Middle East. At least a sampling of TA456 malware is attributed to an individual employed by MRA, a company with ties to the Islamic Revolutionary Guard Corps.”
The recent revelations come as a timely reminder that cyber criminals have previously successfully exploited the ongoing COVID-19 pandemic.
[Related: Chinese hackers target swathe of French organisations, French cyber agency raises security alarm]

Liam Garman
Liam Garman is the managing editor of professional services, real estate and security at Momentum Media. He began his career as a speech writer at New South Wales Parliament before working for world leading campaigns and research agencies in Sydney and Auckland. Throughout his career, Liam has managed and executed international media campaigns spanning politics, business, industrial relations and infrastructure. He’s since shifted his attention to writing on politics and business, and holds a Bachelor of Commerce from the University of Sydney and a Masters from UNSW Canberra with a thesis on postmodernism and media ecology.